In the information technology area, the most common Managed IT services appear to evolve around connectivity and bandwidth, network monitoring, security, virtualization, and disaster recovery. Beyond traditional application and infrastructure management, Managed IT Services may also include storage, desktop and communications, mobility, help desk, and technical support and everything for technology up-keep.
FIXING ISSUES BEFORE THEY HAPPEN
Fortinet Firewall Deployment

Fortinet Firewall Deployment provides powerful protection across the entire attack surface. Engage us to help you lower your risk and own strong security.
Hyper V Cluster

Hyper V Cluster provides the ability to rapidly move virtual machines from one to another. We got this!
365 Email

Office 365 is the capability to work from anywhere as long as you have internet connectivity “WORK ANYWHERE”.
Email Migration

Email migration is a process in which an email or multiple email messages are migrated from one email client to another email client. Do not worry! Our team does this for you without any drawback.
P2V, V2P or P2P Migration
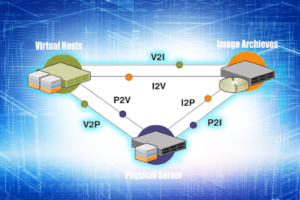
Vedd Tech team helps your organisation to create a virtual machine in a virtual host environment and copy all the files from OS, applications and data from the source machine.
Windows Server Installation

Although upgrade installs are possible, your server will be more stable if you perform a new install. Do not worry. Our team is here to assist you.
Virus Threat Protection

We’ve Got This! Virus & Threat protection in Windows Security helps you scan for threats on your device. Antivirus Software is a data security utility that is installed in a computer system to protect your device by scanning for malware, viruses, and cyber and security threats. It detects or recognizes the virus, and then after detecting the presence of the virus, it works on removing it from the computer system. Antivirus also prevents any potential virus from infecting your computer in the future. Get antivirus software so you can use your computer without the continuous fear of falling prey to a virus attack.
VMWare Cluster
We manage this for you! – A cluster is a group of hosts. When a host is added to a cluster, the host’s resources become part of the cluster’s resources. The cluster manages the resources of all hosts within it. Clusters enable the vSphere High Availability (HA) and vSphere Distributed Resource Scheduler (DRS) solutions.
License Renewal

When your software licenses are expiring, do not worry!
Leave it to us. Once the maintenance agreement is signed; we keep a record of all your licenses and the updates and expiry. Our team will keep monitoring and provide reminders. We assist you to make your burden lesser by renewing those licenses once approval is given.
Project Completion & Proper Documentation

Once all IT issues are solved, we ensure to provide our client proper documentation of the project completion on all the resources used, reports, cost incurred and maintenance guidance.
Network Attached Storage & Other Storages

Network-attached storage is a file-level computer data storage server connected to a computer network providing data access to a heterogeneous group of clients. NAS is specialized for serving files either by its hardware, software, or configuration. There are many storage solutions available that can best fit your budget, usage, and other requirements. Reach us, we will propose the best storage for your business.
New Server Deployment

One Single Host instead of Many Servers – Efficiency.
Your organization does not need to invest in many servers or hosts for each server role or application server. We got a better solution – More virtual servers in a single host can be done. The server is built to manage all network resources. Servers are often dedicated and engineered to manage, store, send and process data.
Firewall Implementation & Configuration

We implement a firewall as a network security system to monitor and control the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted internal network and an untrusted external network, such as the Internet.
IT Troubleshooting

Vedd Tech does troubleshooting to identify or diagnose “trouble” in the management flow of a system or machine caused by a failure that occurs. We troubleshoot and eliminate the potential causes of a problem. The problem is initially described as symptoms of malfunction, and troubleshooting is the process of determining and remedying the causes of these symptoms. Troubleshooting is a form of problem-solving. Finally, after troubleshooting, our team confirms that the solution restores the product or process to its working state.
Windows Server Maintenance

Simple maintenance and monitoring can often prevent a server failure from turning into a server disaster. Server maintenance needs to be performed frequently to ensure that your server will continue to run with minimal problems. Most of the maintenance tasks are automated within the Windows operating system. However, there are still things that need to be checked and monitored regularly to ensure that Windows is running optimally. We at Vedd Tech perform all the steps that should be taken to maintain your servers such as server updates, security, backups, monitoring, file system maintenance, and other general tasks like monitoring event logs and statistics, weekly or monthly regular scans, and checking server reliability.
VPN SetUp & Remote Access

A VPN allows you to create a secure connection to another network over the Internet.
VPNs can be used to access region-restricted websites, shield your browsing activity from prying eyes on public Wi-Fi, and more. You can use a VPN to; Connect business networks securely over the internet; Allow you to access a business network from home; Bypass geographic restrictions on websites or streaming audio and video; Watch streaming media like Netflix and Hulu; Protect yourself from snooping on untrustworthy Wi-Fi hotspots; Gain at least some anonymity online by hiding your true location; Protect yourself from being logged while torrenting.
Network Infrastructure (Cabling, Switching & Data Point)

Network infrastructure is part of the IT infrastructure. Vedd Tech ensures the entire network infrastructure is interconnected and can be used for internal communications, external communications, or both. Network infrastructure includes the below which is all monitored and performed by Vedd Tech.
Networking Hardware – Routers, Switches, LAN cards, Wireless routers, Cables.
Networking Software – Network operations and management, Operating systems, Firewall, Network security applications.
Network Services – T-1 Line, DSL, Satellite, Wireless protocols, IP addressing.

WHAT IS MANAGED IT SERVICES?
Managed IT Services is when you outsource your business’s Information Technology (IT) to a trusted IT company which in turn provides your employees unlimited IT support while proactively and strategically managing your IT infrastructure – all at a fixed price.
EFFECTIVELY MONITOR & MANAGE CLIENTS' NETWORK
- Outsource the responsibility for maintaining and anticipating need for a range of processes and functions in order to improve client’s operations and cut expenses.
- IT support package that works for you. Specialize in providing quality IT support to small and medium-sized businesses or MNCs.
- Leave your IT service management to the global Managed IT provider so you can focus on your business development.
